Acquire a Public Key Certificate for the Keyfactor Command Server
Keyfactor recommends using HTTPS to secure the channel between clients and the Keyfactor Command server(s). This requires at least one SSL![]() TLS (Transport Layer Security) and its predecessor SSL (Secure Sockets Layer) are protocols for establishing authenticated and encrypted links between networked computers. certificate. You will need an SSL certificate or certificates for each of the hostnames you have identified (see Hostname Identification and Resolution).
TLS (Transport Layer Security) and its predecessor SSL (Secure Sockets Layer) are protocols for establishing authenticated and encrypted links between networked computers. certificate. You will need an SSL certificate or certificates for each of the hostnames you have identified (see Hostname Identification and Resolution).
Acquire the certificate(s) using the Fully Qualified Domain Name (FQDN) of the server or alias used for the Keyfactor Command server(s). For example:
keyfactor.keyexample.com
The certificate(s) may be installed on the Keyfactor Command server(s) prior to installation of the Keyfactor Command software or may be installed at the time of Keyfactor Command installation. See Configure SSL for the Default Web Site on the Keyfactor Command Server for more information.
If installed ahead of time, the certificate(s) should be placed in the Personal Certificate store of the Local Computer using the Certificates MMC Snap-In.
Application-Level Encryption
Keyfactor Command uses data encryption for sensitive data—such as private keys for certificates—stored in the Keyfactor Command database (see SQL Server). This option encrypts only the data in the database deemed to be of a sensitive nature, not the entire database. By default, the data is encrypted using SQL encryption, but you have the option to add another level of security with application-level encryption. If you choose to enable this option, you will need a certificate for this purpose installed in the Personal Certificate store of the Local Computer on each Keyfactor Command server. The certificate must have a key usage of either key encipherment or data encipherment enabled. Microsoft certificate templates only allow you to configure data encipherment ("Allow encryption of user data") as a suboption to key encipherment ("Allow key exchange only with key encryption"). You do not need to enable both. You may use the certificate acquired in the name of the Keyfactor Command web site (assuming it supports the appropriate key usage) or you may enroll for a separate certificate for this purpose. The same certificate must be used on all Keyfactor Command servers and the certificate must be available in the certificate store on the machine when you run the Keyfactor Command installation. A hardware security module (HSM) may be used, if desired. To support the use of an HSM, the Windows CSP driver for the HSM must be installed on the Keyfactor Command server. Be aware that transactions accessing the encrypted data—such as enrolling for PFX![]() A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers. certificates, downloading PFX certificates, running inventory, and adding certificates to certain types of certificate stores (e.g. F5, NetScaler)—will require accessing the HSM. A slow HSM will slow down these processes.
A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers. certificates, downloading PFX certificates, running inventory, and adding certificates to certain types of certificate stores (e.g. F5, NetScaler)—will require accessing the HSM. A slow HSM will slow down these processes.
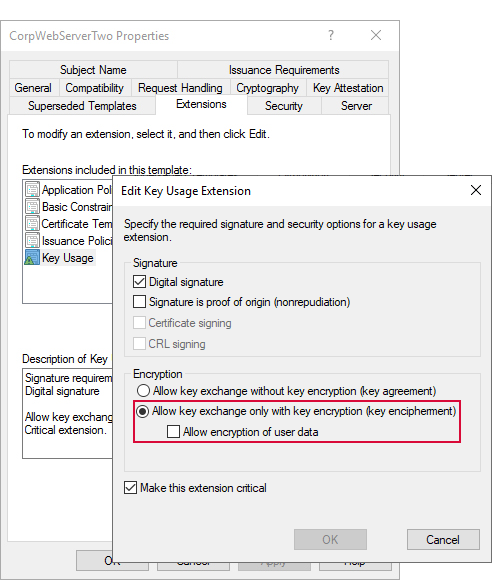
Figure 444: Certificate Template with Key Encipherment Key Usage

